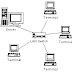
Star topology is centralized and likened topologies similiar to the star. In a star topology, all the cables from computers connected to a central location, where everything is connected to a device called hub.

Star topology is used in dense networks, while endpoint can be reached directly from a central location, the need for network expansion, and requires high reliability. This topology is the arrangement that using more cable than bus and because of all the computers and devices connected to a central point. So if there is one computer or device that is corrupt, the other will not affect the network.
How Star Network Work?
Every computer in star network to communicate with central hub that sends back messages to all computers (in a broadcast star network) or only to the destination computer (in switched star network). Hub of a broadcast star network can be active or passive. Active hub renew the electrical signal that is received and sends it to all computers connected to the hub. Hub types are often also called multiport repeater. If we use the hub has 32 ports, if all ports filled, then the collision will often occur that would result in decreased of network performance. To avoid this we can use a switch that has the ability to define an destination data. Active hub and switch requires power to run it. Pasisive hubs, like wiring panels or punch-down block, only serves as a connection point (connection point) and did not renew the reinforcement signal or signals. Passive hubs do not requires electricity to run it.
To build a network using this topologies, you requires a higher cost than bus or ring topologies because it requiresmore wires to connect each computer to a hub or switch.however, this topology is very easy to fix if problems occuron the network. This topologies is used almost in everyoffice, school, and internet cafe.

 08.10
08.10
 pull email
pull email




 probably a bit difficult to find a network that still uses this cable. because the
probably a bit difficult to find a network that still uses this cable. because the